To answer this question, let’s begin by acknowledging the similarity between the two. Both tests are designed to reveal weaknesses in your organisation’s security posture. Fundamentally, they differ in three ways: scope, goals and approach.
Scope
A penetration test targets one element of your IT environment. For example, your network, web application, wireless solution or mobile app.
The scope of a red team is considerably broader. As well as seeking to identify holes in your electronic defences, they may try to breach your physical perimeters or socially engineer your users to gain access to your systems.
Goals
The goal of a penetration tester is to identify the security vulnerabilities of the target system. A red team takes this a step further. Their objective is ostensibly to steal your assets – for example, your client lists, intellectual property or financial information.
Approach
While both tests are highly controlled, a penetration tester will work with your IT team to facilitate the testing. Conversely, a red team is adversarial: they will go head to head with your in-house team. For added realism, only two or three people in your organisation may even know that a red team has been engaged.
When Attack is the Best Form of Defence
By deploying similar strategies, tactics and hacking tools as real-life cyber criminals, a red team will give you an authentic picture of your organisation’s defences. The detection and response capabilities of your IT department will be pushed to their limits, affording invaluable learning opportunities.
As the saying goes however, you’re only as strong as your weakest link. Perspective Risk - an IT Lab company – has a 100% success rate breaching physical perimeters. During one engagement, our security consultant - disguised as a delivery driver – gained access to the client’s offices. Within minutes, he was inside the unlocked server room.
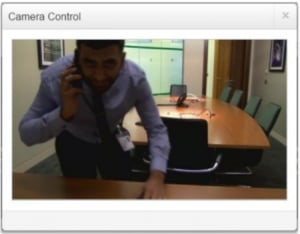
A Perspective Risk (IT Lab company) Red Team Engagement
He also spent time in the company’s meeting room (pictured) and logged in to their teleconferencing system using the manufacturer’s default credentials, which hadn’t been changed.
So, the short answer to the question posed by this blog is a resounding yes. But this should be considered in context with your organisation’s current security posture.
For organisations with established security systems and policies, a red team engagement is a highly effective way of challenging them. Additionally, it may break down some of the beliefs and assumptions surrounding their effectiveness.
However, if your company’s security is still maturing, a red team exercise is an expensive way of identifying your vulnerabilities. Instead, focus on your critical assets and begin pragmatically but swiftly. For example, consider:
- Penetration testing for the mobile app that’s generating business, or the wireless solution that you worry isn’t as watertight as it should be. Download A Buyer’s Guide to Penetration Testing.
- If you’re unsure where best to start, a security consultant will help you to understand where your value lies, and who might want to take it from you. Learn about cyber security strategy and consultancy.
- Good cyber hygiene – ensure the basics are covered with Cyber Essentials or Cyber Essentials PLUS certification.
- Your user base – and often your first line of defence. Educate them with social engineering and user awareness training.
And with the relentless onslaught on UK PLC, it’s clear that cybersecurity is a growing imperative. For help with any aspect of your security and to be put in touch with our expert team, click here to contact us.






