As Cybercriminals Exploit the Coronavirus, Don't Be Caught Out
The coronavirus is evoking the Blitz spirit and bringing out the best in many. Sadly, there are others taking advantage of the deepening crisis: cybercriminals. Our Cyber Security Operations Manager shares two SPAM email examples and tells what to watch out for.

As organisations across the UK begin to take up social distancing and remote working, the risk of a cyber-attack and compromise against individuals and businesses is expected to rise.
The IT Lab Cyber Security Operations Centre (CSOC) has observed cyber criminals actively exploiting the urgent need for information on the emergency through coronavirus-themed campaigns including the development of malicious apps, fraudulent outbreak map websites and phishing emails.
The heightened interest in the news relating to the virus has resulted in an increase in social engineering with cybercriminals targeting individuals and businesses with fake emails. These promise important information when, in reality, they're designed to deliver malware to steal your credentials or infect your machine for other malicious purposes.
- Be aware of emails sent from @coronavirus[.]*** addresses (or similar) and if it is hyperlinked in an email.
- Treat websites and apps that claim to be mapping and monitoring the coronavirus outbreak with extreme caution as there are a number known to be actively delivering malware.
- Be aware of email messages claiming to be from the World Health Organisation (WHO), UK government or HM Revenue and Customs (see the reported examples below):
Example SPAM Email Messages
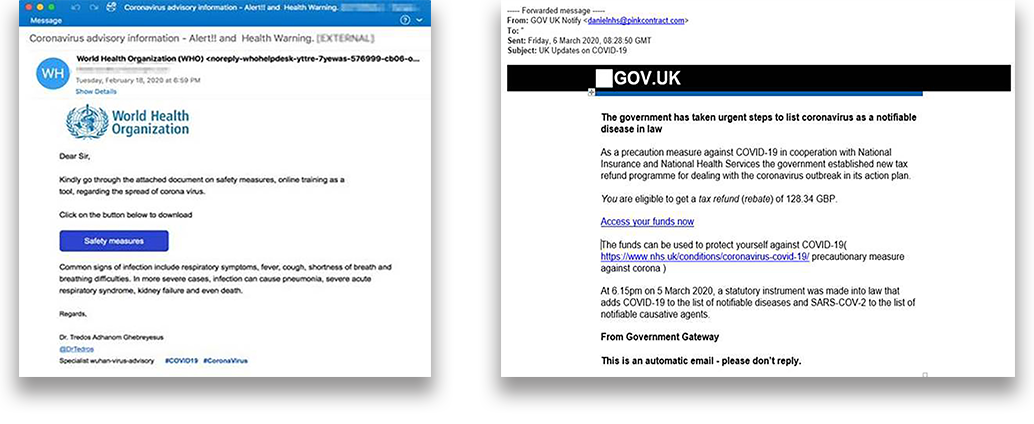
If you receive any form of questionable communication (phone call, email, SMS, etc.) report it to your cybersecurity team or provider for investigation at the earliest possibility.
Our Cyber Security Operations Centre is continuously monitoring and evaluating the cyber threat landscape and will provide updates as the situation continues to evolve.





